Social engineering attacks trick people into sending dollars or information to hackers or granting them access to sensitive methods. Common social engineering ways consist of:
On the other close on the hacking spectrum, the cybersecurity Neighborhood will depend on ethical hackers—hackers with helpful rather than criminal intentions—to check protection actions, tackle protection flaws and prevent cyberthreats.
Utilize a VPN Employing a Digital private network (VPN) will allow people to browse the net securely. It hides their site and stops hackers from intercepting their information or browsing activity.
AARP is often a nonprofit, nonpartisan Corporation that empowers people to choose how they Reside since they age.
In any other case often called the Morris Worm of 1986, the incident was intended to highlight protection vulnerabilities but inadvertently brought about intensive hurt that lasted for numerous times.
Leverage encryption – Even when hackers efficiently obtain a corporation's community, encryption can proficiently avert them from breaching or accessing any info.
Other messages could appear to be They may be coming from a bank or A further business, saying there’s been a hack, possibly fraudulent exercise, or other problem, in a scam intended to get your account or individual data.
Whether or not these hackers are ethical or malicious is in the attention of your beholder. Consider the Stuxnet attack on Iranian nuclear facilities, considered to get the perform with the US and Israeli governments. Anybody who views Iran's nuclear method for a security threat may possibly think about that assault moral.
As an example, if a hacker gains usage of a device’s command-line interface, they could run destructive scripts instantly during the gadget’s memory with out leaving Significantly of the trace.
Put in antivirus and anti-malware computer software – Software package programs that detect and take away viruses and malware are crucial in guarding your computer system and making certain your data is Harmless.
Our mission is preserving the public from misleading or unfair business procedures and from unfair ways of Opposition as a result of law enforcement, advocacy, research, and schooling.
A charity scam is whenever a thief poses as an actual charity or can make up the identify of a charity that Appears actual to obtain funds from here you.
Hackers are motivated by personal acquire, to help make a statement, or merely since they can. Examine additional under and defend your self from hackers currently.
7 million. While this historic hack towards two of quite possibly the most well known U.S. governmental businesses experienced minor damaging effects In general, the teen's steps resulted in NASA's networks shutting down for 3 weeks.
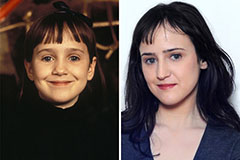 Mara Wilson Then & Now!
Mara Wilson Then & Now!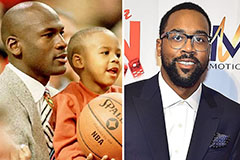 Marcus Jordan Then & Now!
Marcus Jordan Then & Now! Raquel Welch Then & Now!
Raquel Welch Then & Now! Mary Beth McDonough Then & Now!
Mary Beth McDonough Then & Now! Nicholle Tom Then & Now!
Nicholle Tom Then & Now!